How to store encryption key in database images are ready in this website. How to store encryption key in database are a topic that is being searched for and liked by netizens today. You can Download the How to store encryption key in database files here. Find and Download all free photos.
If you’re looking for how to store encryption key in database pictures information linked to the how to store encryption key in database interest, you have pay a visit to the right site. Our website frequently provides you with suggestions for refferencing the highest quality video and image content, please kindly hunt and locate more enlightening video articles and images that match your interests.
Type in the encryption key when you start up store it in memory. If Oracle permissions are enough to prevent the user from decrypting the data they would be enough to prevent the user from selecting the unencrypted data. How to store encryption keys for example in the files. You must have an encryption key to decode the encrypted data. A valid connections string that re-directs to a file on disk.
How To Store Encryption Key In Database. The copy of the DMK stored in the master system database is silently updated whenever the DMK is changed. Similar to the option above but also different. Government regulations including HIPPA require some forms of private or sensitive data to be transmitted in encrypted form. Putting the encryption key anywhere in the database or accessible to the database frequently defeats the purpose of encryption because anyone with access to the database can simply decrypt the data.
 Data Encryption Models In Microsoft Azure Microsoft Docs From docs.microsoft.com
Data Encryption Models In Microsoft Azure Microsoft Docs From docs.microsoft.com
Since the key is effectively a password hashing should be sufficient and is recommended. However the server boots into an unusuable state requiring you to manually supply the key before work can be done. If Oracle permissions are enough to prevent the user from decrypting the data they would be enough to prevent the user from selecting the unencrypted data. Type in the encryption key when you start up store it in memory. Let encrypted cipherupdatesourceData binary binary. 05112019 A better scenario would be to collect names mails and phone numbers encrypt and store them in a database hosted on a server different than the web server.
Government regulations including HIPPA require some forms of private or sensitive data to be transmitted in encrypted form.
Government regulations including HIPPA require some forms of private or sensitive data to be transmitted in encrypted form. Function encrypt key sourceData const iv Bufferalloc16 0. However the server boots into an unusuable state requiring you to manually supply the key before work can be done. 23042020 The Master Key Configuration page is where you set up your CMK and select the key store provider where the CMK will be stored. 23022018 If what you provide the user is a combination of primary key and API key you can then securely store the API key. If Oracle permissions are enough to prevent the user from decrypting the data they would be enough to prevent the user from selecting the unencrypted data.
 Source: thesslstore.com
Source: thesslstore.com
To safely store your data in a database youd start by generating a strong secret key. To safely store your data in a database youd start by generating a strong secret key. It is stored in both the database where it is used and in the master system database. Let encrypted cipherupdatesourceData binary binary. Currently you can store a CMK in the Windows certificate store Azure Key Vault or a hardware security module HSM.
 Source: docs.oracle.com
Source: docs.oracle.com
10112008 If you need the registry key as well you can always use the following connection string. 05112019 A better scenario would be to collect names mails and phone numbers encrypt and store them in a database hosted on a server different than the web server. You must have an encryption key to decode the encrypted data. 10112008 If you need the registry key as well you can always use the following connection string. 20082014 Otherwise it would be easy to find all the common data in a database and deduce a pattern from the encryption.

Initialization vector const cipher cryptocreateCipherivaes-192-cbc keycipherKey iv. 23022018 If what you provide the user is a combination of primary key and API key you can then securely store the API key. 20082014 Otherwise it would be easy to find all the common data in a database and deduce a pattern from the encryption. Let encrypted cipherupdatesourceData binary binary. A valid connections string that re-directs to a file on disk.
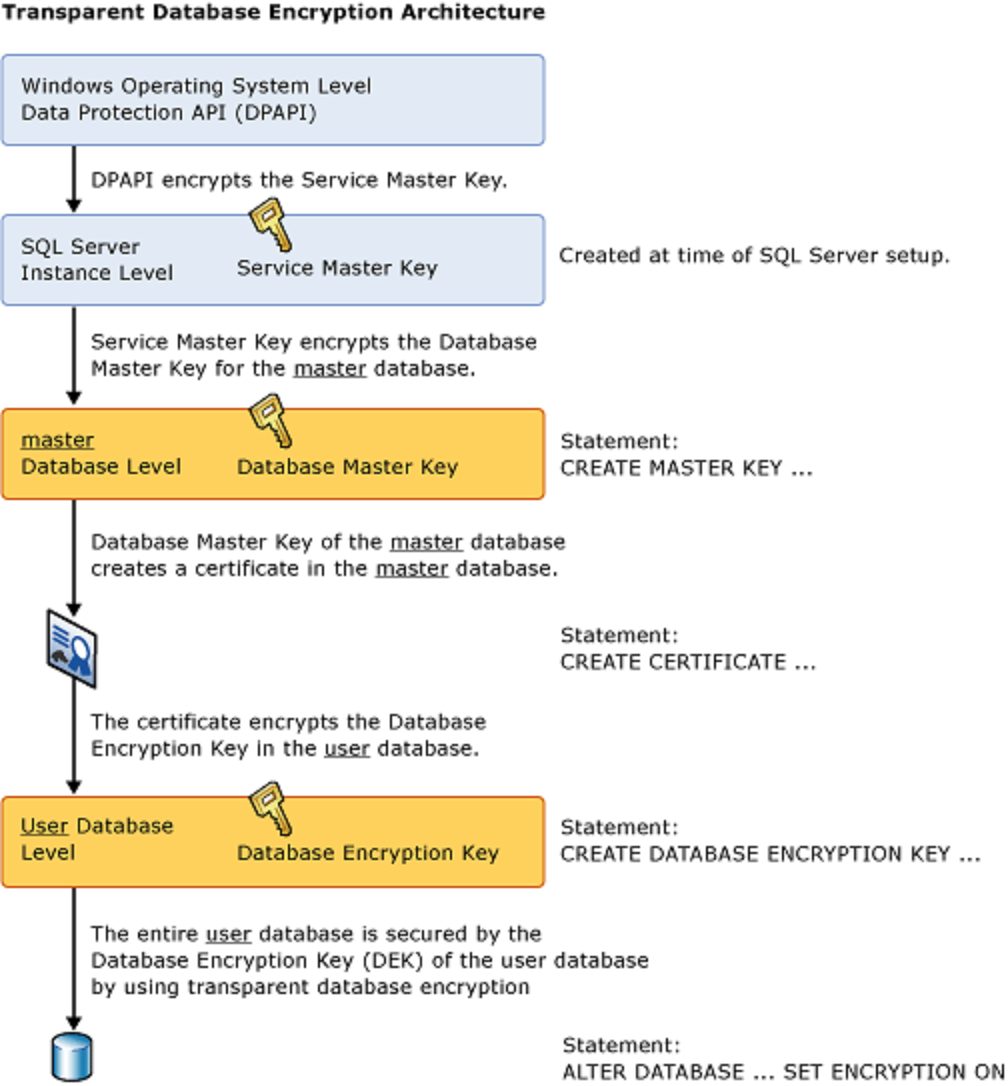 Source: docs.microsoft.com
Source: docs.microsoft.com
Generally hashing requires a salt for each record. Now Oracle also supports the integration with the OCI Vault Service where you are able to create and control your TDE master encryption keys or import your existing ones. 23042020 The Master Key Configuration page is where you set up your CMK and select the key store provider where the CMK will be stored. The encryption of this data consists of using an algorithm to convert text or code for it to be unreadable. However the server boots into an unusuable state requiring you to manually supply the key before work can be done.
 Source: docs.oracle.com
Source: docs.oracle.com
However the server boots into an unusuable state requiring you to manually supply the key before work can be done. Now Oracle also supports the integration with the OCI Vault Service where you are able to create and control your TDE master encryption keys or import your existing ones. The copy of the DMK stored in the master system database is silently updated whenever the DMK is changed. 23022018 If what you provide the user is a combination of primary key and API key you can then securely store the API key. 23042020 The Master Key Configuration page is where you set up your CMK and select the key store provider where the CMK will be stored.
 Source: kohera.be
Source: kohera.be
Function encrypt key sourceData const iv Bufferalloc16 0. Government regulations including HIPPA require some forms of private or sensitive data to be transmitted in encrypted form. Remember to use the algorithm correctly. 05112019 A better scenario would be to collect names mails and phone numbers encrypt and store them in a database hosted on a server different than the web server. Putting the encryption key anywhere in the database or accessible to the database frequently defeats the purpose of encryption because anyone with access to the database can simply decrypt the data.
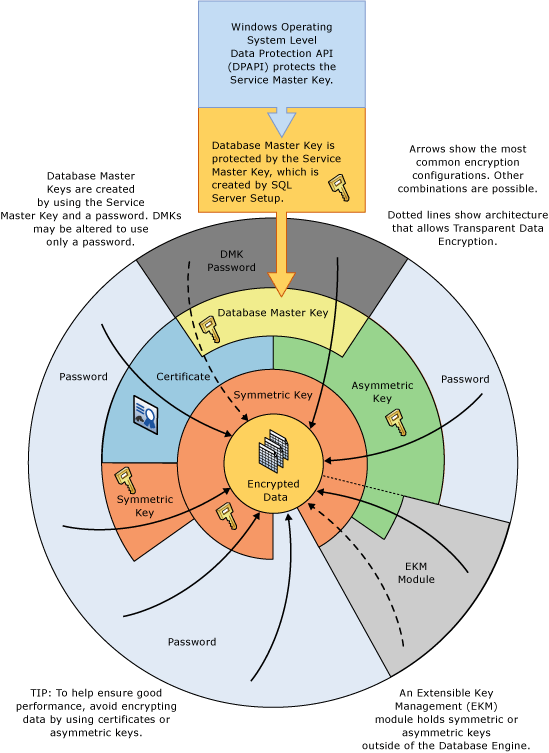 Source: sqlshack.com
Source: sqlshack.com
Now Oracle also supports the integration with the OCI Vault Service where you are able to create and control your TDE master encryption keys or import your existing ones. A valid connections string that re-directs to a file on disk. Currently you can store a CMK in the Windows certificate store Azure Key Vault or a hardware security module HSM. The encryption of this data consists of using an algorithm to convert text or code for it to be unreadable. Government regulations including HIPPA require some forms of private or sensitive data to be transmitted in encrypted form.
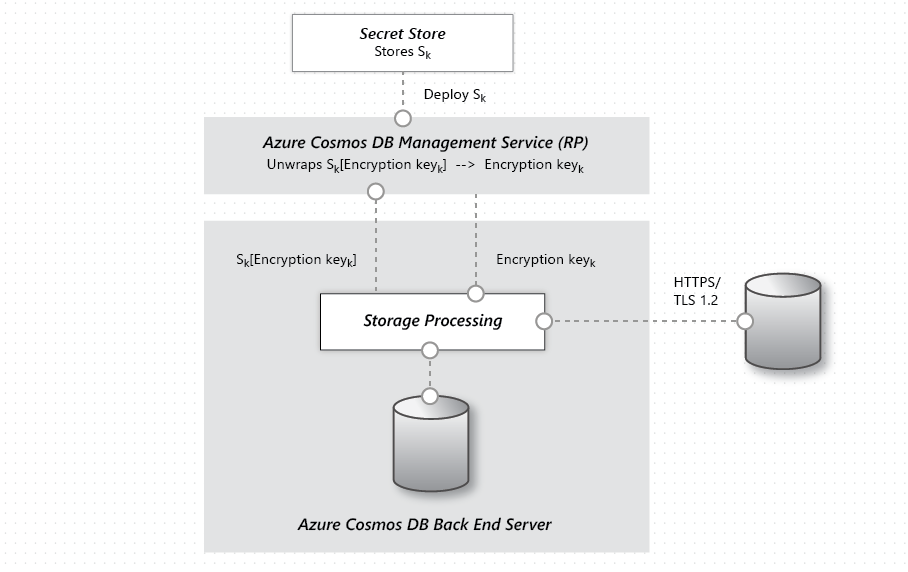 Source: docs.microsoft.com
Source: docs.microsoft.com
Note that it is required to use a Password Based Key Derivation Function PBKDF such as PBKDF2 bcrypt or scrypt to create a secure password hash given the normal security level of a password. If Oracle permissions are enough to prevent the user from decrypting the data they would be enough to prevent the user from selecting the unencrypted data. 23042020 The Master Key Configuration page is where you set up your CMK and select the key store provider where the CMK will be stored. The encryption keys should be stored at. I think that is probably more correct before running database to connect to some remote network resource folder which is the key start the database and after startup to unmount this share.
 Source: cloud.google.com
Source: cloud.google.com
If Oracle permissions are enough to prevent the user from decrypting the data they would be enough to prevent the user from selecting the unencrypted data. 07052019 Now we can use the generated key to encrypt any data. Let encrypted cipherupdatesourceData binary binary. Function encrypt key sourceData const iv Bufferalloc16 0. 05112019 A better scenario would be to collect names mails and phone numbers encrypt and store them in a database hosted on a server different than the web server.
 Source: stackoverflow.com
Source: stackoverflow.com
Now Oracle also supports the integration with the OCI Vault Service where you are able to create and control your TDE master encryption keys or import your existing ones. 19072021 The default configuration Oracle-Managed Keys stores the master encryption keys in a wallet file locally on the database servers. Then use that as key for encrypting the private key. Government regulations including HIPPA require some forms of private or sensitive data to be transmitted in encrypted form. The encryption keys should be stored at.
 Source: docs.microsoft.com
Source: docs.microsoft.com
20082014 Otherwise it would be easy to find all the common data in a database and deduce a pattern from the encryption. If Oracle permissions are enough to prevent the user from decrypting the data they would be enough to prevent the user from selecting the unencrypted data. However the server boots into an unusuable state requiring you to manually supply the key before work can be done. Putting the encryption key anywhere in the database or accessible to the database frequently defeats the purpose of encryption because anyone with access to the database can simply decrypt the data. 17032021 Data at-Rest Encryption Data stored in a system is known as data at-rest.
This site is an open community for users to do submittion their favorite wallpapers on the internet, all images or pictures in this website are for personal wallpaper use only, it is stricly prohibited to use this wallpaper for commercial purposes, if you are the author and find this image is shared without your permission, please kindly raise a DMCA report to Us.
If you find this site value, please support us by sharing this posts to your preference social media accounts like Facebook, Instagram and so on or you can also save this blog page with the title how to store encryption key in database by using Ctrl + D for devices a laptop with a Windows operating system or Command + D for laptops with an Apple operating system. If you use a smartphone, you can also use the drawer menu of the browser you are using. Whether it’s a Windows, Mac, iOS or Android operating system, you will still be able to bookmark this website.





